
In an era of advanced cyber threats, endpoint security has become indispensable for businesses of all sizes. Endpoint devices, like laptops, desktops, smartphones, and servers, are essential for daily business activities, but they also represent one of the weakest links in cybersecurity. Cybercriminals constantly exploit these vulnerabilities to launch malware, ransomware, and phishing attacks.
The importance of endpoint security has skyrocketed as attacks grow more targeted and sophisticated. Traditional antivirus solutions are no longer sufficient to handle the complexity of modern threats. Businesses need a robust, proactive, and adaptive approach to stay secure.
This is where Cisco Secure Endpoint steps in. Designed to address the challenges of today’s threat landscape, it provides a unified and advanced solution for endpoint security. By combining powerful detection tools, real-time threat intelligence, and seamless integration with broader security frameworks, Cisco Secure Endpoint is a must-have for businesses aiming to safeguard their critical assets.

So, what is Cisco Secure Endpoint? A Cisco Secure Endpoint is a cloud-delivered endpoint security platform that goes beyond basic antivirus functionality. It is engineered to provide comprehensive protection by incorporating advanced features like Endpoint Detection and Response (EDR), threat hunting, and multi-domain threat management.
Unlike traditional endpoint solutions, which focus on detecting known threats, Cisco Secure Endpoint excels in identifying unknown and emerging threats using machine learning, global threat intelligence, and behavioral analytics. It empowers organizations to not only detect attacks but also to respond swiftly, reducing the time and impact of security incidents
Cisco Secure Endpoint is packed with features that make it a standout solution in the endpoint security market:
This combination of advanced tools ensures that businesses remain resilient against a constantly evolving cyber threat landscape.
Cisco Secure Endpoint is built on four pillars: Prevent, Detect, Respond, and Maximize. Each pillar offers distinct capabilities that strengthen endpoint security.
Proactively preventing attacks is a cornerstone of effective endpoint security. Cisco Secure Endpoint employs cutting-edge technologies to stop threats before they can cause damage:
This proactive approach minimizes the attack surface and reduces the likelihood of successful breaches.
Detecting threats quickly is essential to minimize damage. Cisco Secure Endpoint integrates several advanced detection capabilities:
With these tools, businesses can uncover even the most elusive threats and act decisively.
A fast and efficient response to threats is crucial for minimizing damage. Cisco Secure Endpoint enhances response capabilities with:
These features enable organizations to contain and resolve security incidents with minimal disruption.
Cisco Secure Endpoint doesn’t just protect—it also helps organizations maximize their security capabilities:
Cisco Secure Endpoint offers a tiered approach to endpoint security, ensuring organizations of all sizes can find the right solution to meet their needs. The three tiers—Essentials, Advantage, and Premier—are designed to provide increasing levels of protection and advanced features. Below is a breakdown of what each tier offers:
| Plan | Features | Best For |
| Essentials | Core antivirus, endpoint isolation | Small businesses |
| Advantage | Advanced search, risk-based analytics, malware insights | Growing organizations |
| Premier | Talos Threat Hunting, private cloud, full EDR | Large enterprises |
This tiered approach allows businesses to choose the plan that best aligns with their size, goals, and security needs.
Cisco Secure Endpoint offers a range of advantages that set it apart from traditional endpoint security solutions. Its integrated approach, efficiency-focused tools, and customizable deployment options make it a standout choice for organizations of all sizes and industries.
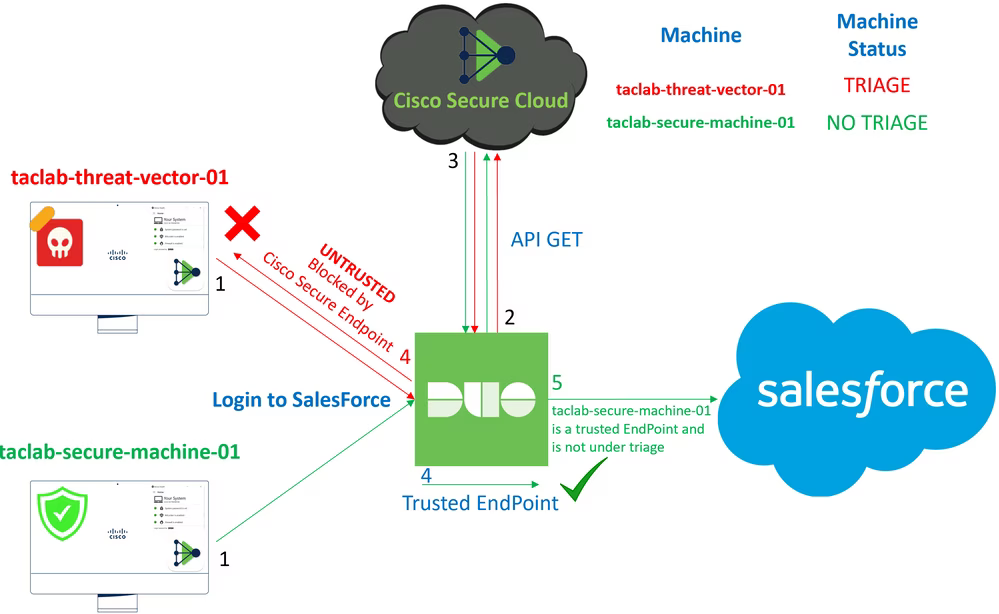
Cisco Secure Endpoint’s strength lies in its seamless integration with the broader Cisco security ecosystem, including email, web, and network security solutions. This unified approach to endpoint security allows organizations to consolidate their cybersecurity defenses under a single, cohesive platform.
By eliminating the need for multiple disparate tools, Cisco Secure Endpoint simplifies management, reduces costs, and ensures no gaps exist in the defense strategy. Whether protecting endpoints from advanced threats or securing email and web gateways, Cisco provides comprehensive coverage, safeguarding all attack surfaces.
This interoperability extends to third-party tools, making it easy for businesses to incorporate Cisco Secure Endpoint into their existing IT infrastructure. This adaptability ensures scalability and allows organizations to optimize their endpoint security without overhauling their systems.
Efficiency is a defining characteristic of Cisco Secure Endpoint, empowering businesses to respond to threats faster and more effectively.
These efficiency gains translate to reduced operational downtime, enhanced productivity, and better resource allocation, giving businesses a competitive edge.
Recognizing that businesses have diverse security requirements, Cisco Secure Endpoint offers flexible deployment models:
These options ensure that organizations, regardless of size or IT resources, can benefit from Cisco Secure Endpoint’s advanced security features.
Cisco Secure Endpoint leverages cutting-edge technologies to deliver unparalleled endpoint protection. These technologies work synergistically to provide real-time visibility, proactive defense, and efficient response.
At the heart of Cisco Secure Endpoint lies Talos Threat Intelligence, one of the world’s largest commercial threat intelligence teams. Talos analyzes millions of threats daily, identifying new malware, vulnerabilities, and attack vectors. This global perspective ensures that Cisco Secure Endpoint is always up-to-date with the latest threat intelligence, providing proactive defense against emerging cyberattacks.
Cisco’s Extended Detection and Response (XDR) aggregates and correlates data from endpoints, email, cloud workloads, and networks. This comprehensive approach provides a unified view of security incidents, enabling organizations to identify patterns and potential threats across their entire infrastructure. By breaking down silos and enhancing visibility, XDR empowers faster and more accurate threat detection.
Cisco Secure Endpoint’s Managed Detection and Response (MDR) service is a game-changer for businesses with limited IT resources. Cisco’s security experts monitor threats, analyze incidents, and provide rapid response 24/7. This service ensures that businesses are protected around the clock, even when internal teams are unavailable.
The Orbital Advanced Search feature offers real-time visibility into endpoint activity. IT teams can run custom queries to investigate suspicious behavior, uncover hidden threats, and gain deeper insights into security incidents. This capability enhances incident response and helps businesses maintain a proactive security posture.
Cisco Secure Endpoint is designed for flexibility, ensuring smooth implementation across various environments.
Organizations can choose from cloud-based, on-premises, or hybrid deployment options. The cloud-based model offers simplicity and scalability, while the on-premises option provides additional control for businesses with strict compliance requirements.
Cisco Secure Endpoint seamlessly integrates with existing Cisco infrastructure, such as Cisco Meraki, as well as third-party tools. This compatibility ensures that businesses can enhance their security without disrupting current workflows or investments.
The platform’s intuitive dashboard provides centralized visibility into endpoints, making it easy for IT teams to monitor activity, manage incidents, and generate reports. Even organizations with limited cybersecurity expertise can use Cisco Secure Endpoint effectively.
In our world, where cyber threats constantly grow, endpoint security is not a luxury—it’s a necessity. Cisco Secure Endpoint offers a unified, efficient, and customizable solution that empowers businesses to protect their most valuable assets. Don’t wait until it’s too late. Take the first step toward comprehensive endpoint protection by exploring Cisco Secure Endpoint. Equip your organization with the tools to detect, prevent, and respond to threats effectively.
At Stratus Informational Systems, we specialize in helping businesses implement and optimize solutions like Cisco Secure Endpoint to ensure robust endpoint security.
Whether you’re exploring your options, need assistance with deployment, or want to integrate Cisco Secure Endpoint into your existing infrastructure, our team is here to help.
Contact us today for a personalized consultation, and let us guide you in fortifying your endpoints with industry-leading protection. Secure your future with the trusted expertise of Stratus Informational Systems—because your security is our priority.

Stay informed about our newest releases and updates